حار بيع أنيق مضاد للسرقة الباب
|
Standard Size |
2050*960 (Accept Customization) |
|
Door Leaf Thickness |
68mm (can be customized) |
|
Door Leaf |
Standard 0.8/1.0mm (Accept Customization) |
|
Inner Filling |
Fire door core panel/honeycomb paper(Accept Customization) |
|
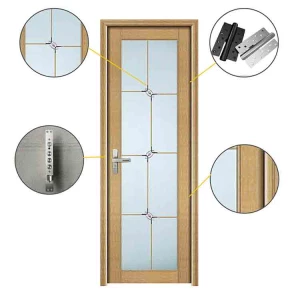
Lock Set |
High Quality Main Lock+Side Lock+Up-Down Lock |
|
Surface Treatment |
Heat Transfer(Accept Customization) |
|
Open Direction |
Inward/Outward/Left/Right |
|
Accessories |
Handle;Lock;Hinge;Peephole;Door Bell;Bolts |
|
Fuction |
Fireproof; Burglarproof |
Keywords: